Password Generator
Password Suggestion
Disclaimer: The below password is NOT guaranteed to be secure. This password generator is used to generate easy to spell, easy to speak and easy to remember passwords to help improve upon the bad habits of most users. A strickly random string of 12+ characters is always better than the simple password below. If you have a password manager, we strongly encourage using random passwords!
| Good: |
FancyGlove818$$ |
Internal Low to Medium External Low to Medium w/2FA Enforced |
| Better: | Fancy-Glove-818$$ |
Internal Medium (AD Users, Switches, Etc.) External Low w/2FA Recommended External Any w/2FA Enforced |
| Best: | Fancy-Great-Glove-818 |
Internal Any (AD Admins, Firewalls, Etc.) External Any w/2FA Recommended |
Password Analyzer
NOTE: Passwords are never sent to our server. Analysis is done in the browser only!
How does this work?
This page uses the new zxcvbn-ts JavaScript library (based on the DropBox original zxcvbn) to rate your password.
This library was developed by a staffer at DropBox to give a more accurate analysis of password strength. Most sites use rules to determine password strength. For hackers, these rules are meaningless and pose no hinderence.
Examples: P@ssw0rd or Password#1 or L3tm3!n would all be considered strong passwords by most rules. However, hackers are wise to the common letter and number replacement techniques and blow through'em quickly.
This test applies a sample dictionary of common english words and common english names, along with some algorithms similar to what a hacker would use to give you a much more realistic strength score.
Is this test safe?
If we tell you yes, will you believe us? If you know Clarity Technology Group, Inc. and this page is using HTTPS (lock icon in the address bar) then you can probably trust us. However, in practical terms, never trust your real passwords to a website you found on Google. If you're worried, try an example password or something similar to your real password.
On the other hand, general advice notwithstanding, this webpage is safe and your password never leaves your browser. The password strength calculations are done right there at your desk and are never sent to us in any way. If you disconnect your wi-fi or network cable, this test should still function.
Is this test accurate?
In a word, NO. It's much more realistic than the rules based approach, but CPUs are constanly getting faster and hackers are constantly improving their algorithms and dictionaries. Do not consider this a definitive answer, use it more as a guideline. Most likely the speeds have increased by the time you are reading this
What is hashing?
When a website stores your password, it likely hashes it or scrambles it using a specific mathamatic algorithm. This way if someone ever looked at the database, they would see the scrambled results instead of the plain passwords.
If a hacker gets a password list, they use software to de-scramble it with trial and error. Historically, websites used very fast hashing algorithms (SHA1 or MD5). This allowed the sites to log people in quickly, but also allows hackers to attempt billions of combinations per second when de-scrambling and makes almost every password vulnerable.
Websites today are moving to slower hashing algorithms, forcing hackers to take more time to find a match.
Another thing that slows down these de-scramble attempts is having a longer password. Since it's trial and error, it starts with aa, ab, ac, etc. This means the longer the password is, the longer it will take to find it.
One caveat is the hacking community maintains a list of 'common passwords' developed by analyzing large breaches over the years. They will always try this list first. This includes common english words and word combinations along with names (with and without common letter/number replacements). So, even with a 'Slow Hash', something like Tr@nsAm will be broken very quickly.
So what should I do?
Two pieces of advice, first, DO NOT use the same password on multiple websites. When one password list is de-scrambled, hackers will sell that list and your username/password will be tried against other common websites, including banks and social media.
Second, use long passwords (15+ characters) containing either random characters or, if you want something more readable, multiple words (3-4) and a few numbers and/or symbols. If you have trouble remembering longer passwords, use a cloud password manager like LastPass or Dashlane or a non-cloud local application like 1Password. With these applications, you only need to remember one good password and they will remember the rest. If you want help implementing one of these, feel free to Contact Us, we are happy to help!
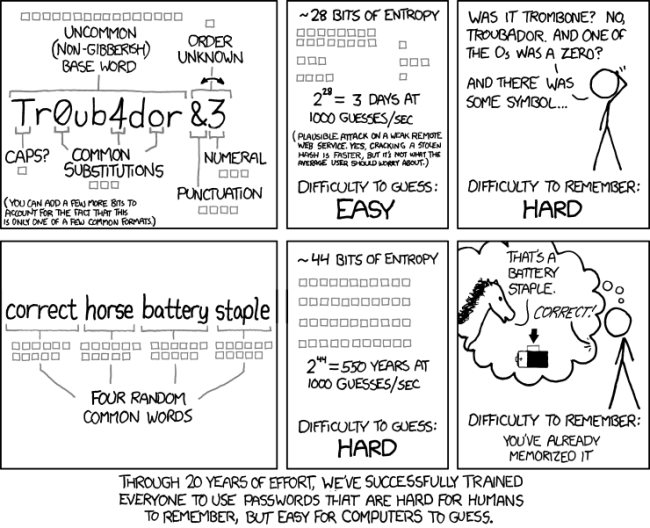
The Illustration (Courtesy of xkcd.com):